It's impossible to create a truly secure Internet: until it's not
The Internet was created without security. Cyber attacks are rampant and our Digital Freedom is at risk. By redefining how the Internet works, Internet3™ reduces cost and delivers trust: At last, Secure Internet instead of Internet Security.

A Global Crisis
Our Digital Freedom is at Risk
Humanity is in the midst of a global crisis: the rise of digital authoritarianism.
Cyber attacks run rampant and articulated threats undermine the credibility and trust of networks. Billions of people still face barriers to access.
We have witnessed nation states who are suppressing freedom of expression, censoring independent news sites, interfering with elections, promoting disinformation and denying citizens other human rights.
Although the current Internet has enabled economic opportunities for billions of people, it also fundamentally hinders the future of our modern economy:
- Without encryption and authentication at its core, Cyberspace is more or less the wild west of our modern economy.
- Too much power is placed in the hands of network administrators who can be coerced by bad actors to shutdown networks or filter information.
- Governments and corporations are forced to utilize private networks which in turn limit innovation and economic freedoms by creating closed networks in the name of security.
- Politically repressive governments have hijacked western technology and are rapidly extending it to create Quasi-Authoritative Ecosystems (QAEs).
Without a solution, key economic partners of the Free World may splinter and join these QAEs – some already have
On cyberspace and emerging technologies, we have a major stake in shaping the digital revolution that’s happening around us and making sure that it serves our people, protects our interests, boosts our competitiveness, and upholds our values.

Tony Blinken
71st U.S. Secretary of State

Reducing Cost and Delivering Trust
Hello, Secure Internet!
Internet3 is the first internet where Security and Authentication comes built-in and in the absence of Internet Service Providers (ISPs), each device owns its IP address making monthly fees obsolete.
This flexibility in cost and security gives power to application developers so that they can focus on building innovative solutions, instead of reinventing the wheel.
Securing Digital Freedom
Internet3 as a technology and solution secures digital democracy by ensuring that cyberspace and digital policy are anchored in democratic principles, openness and human rights. In essence, with Internet3, each device owns its identity in cyberspace and that identity cannot be taken away by anyone.
In partnership and coordination with governments from all around the world, Internet3 provides the basis to build an open digital future where all people can thrive.
We stand strong with the United States and the more than 60 partners from around the globe who launched the Declaration for the Future of the Internet.
A Distributed Multi-Planetary Cyber Society
Internet3 is extremely secure and cost effective because each device generates its own cryptographically-backed IP address.
Instead of paying monthly fees to costly external providers (ISPs), each device owns its IP address, maximizing infrastructure investment.
When users, devices and vehicles can own their own IP address, connectivity can happen anywhere two devices come together, be it in a hot desert, in the air, at sea or even in space.
Compatible with Existing Applications
Internet3 is backwards compatible with today’s popular and best applications.
By communicating with applications via IPv6 system APIs, Internet3 can guarantee that there is no need for application developers to learn anything new.
Most internet applications that you use today will run on top of Internet3.

Real Zero Trust Security
Internet3 is the best way to implement and administer Zero Trust security policy.
Zero Trust, defined by U.S. NIST 800-207, is a security policy requiring all users, whether in or outside the organization’s network, to be authenticated, authorized and continuously validated. Zero Trust assumes that there is no traditional network edge.
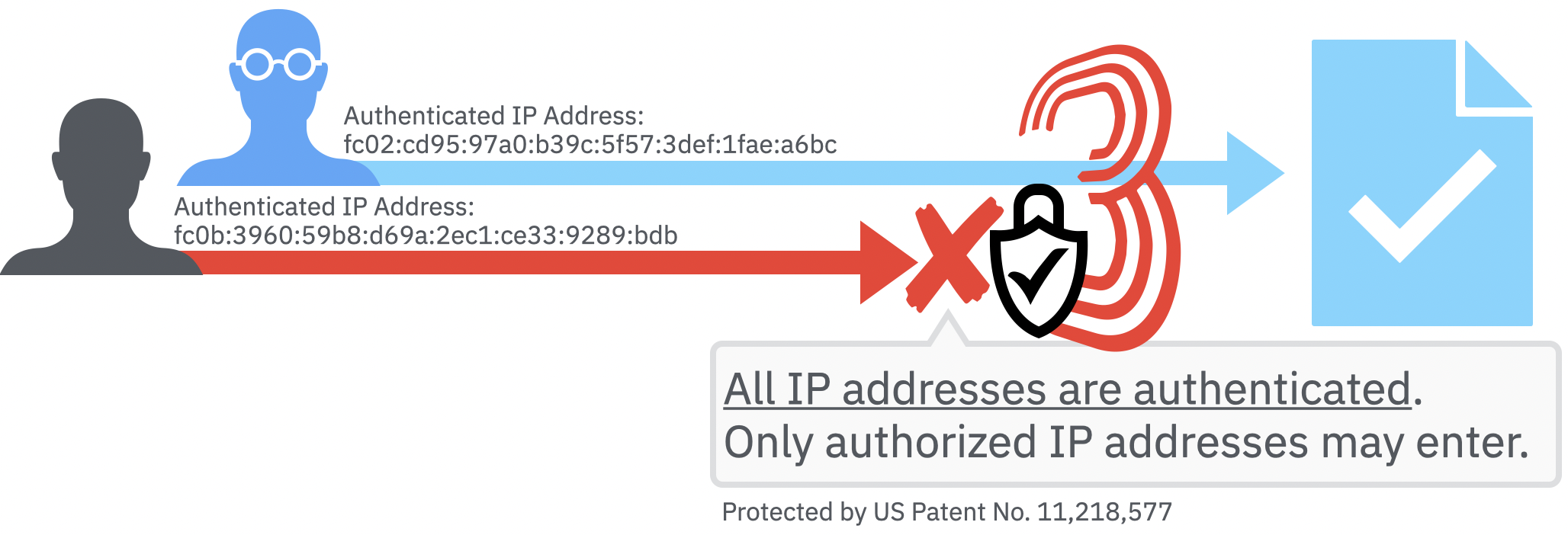
While other solutions require costly software add-ons to enable Zero Trust security, Internet3 provides these guarantees at the IP Address level at no additional cost.
An Accelerator for Embedded and Industrial Markets
The Embedded Industrial World is stuck in the 1980s. Demand for Authentication and Security have not yet been met. Fact: Internet3 is the only internet that can supply Authentication and Security to over one trillion industrial devices at a fixed price. (1 device to 4m2 in urban areas)
With both governments and share holders requiring that corporations integrate new AI and Edge solutions, demand for apps and embedded devices will skyrocket.
Internet3 provides the only truly fixed cost secure foundation.

Based on Proven 3rd Generation Internet Technology
IPv6 is 2nd Generation Internet technology designed to deal with the problem of IPv4 address exhaustion. Internet3 is based on 3rd Generation Internet technology (EVER/IP) which was designed to deal with the problem of the insecurity of IPv6 and the cost of Internet Service Providers.
The major difference is how IP addresses are allocated: IPv6 addresses are allocated from a regional database (IANA), whereas Internet3 addresses are not allocated, but instead generated from a public-private keypair that is owned by each device. Economically, instead of paying monthly fees to costly external providers (ISPs), each device owns its IP address, maximizing infrastructure investment.
This also means that all traffic is encrypted and all devices on the network can be authenticated at the IP address level.
Internet3 addresses have the benefit of backwards compatibility with IPv6 applications with the security of public-key cryptography.



